A number of cybersecurity companies leverage MITRE ATT&CK into their solutions offering. Essentially ATT&CK is a classification system to describe cyberattacks and intrusions, developed by Mitre corporation. It’s no coincidence that MIT is part of the Mitre name since it was spun off from MIT Lincoln Labs, a few miles from us here in Massachusetts That’s a great start and confidence booster. Basic components ATT&CK might be “Phishing for Information” or “System Shutdown”. Most of the time, it’s far more technical.
With a catalog of several hundred attacks classified, organizations can create their own models to help mitigate and remediate vulnerabilities. This could be done with a corporate security policy and/or via a security software platform. For example, Crowdstrike, Jamf Protect, and SenticalOne utilized the MITRE ATT&CK framework in their tools. As each of these ATT&CK entries are numbered and referenced so vendors can reference the malicious techniques using a common understanding and library. IT teams can evaluate and compare the effectiveness of certain solutions, policies, and tools in order to make practical decisions on where to invest time and resources. Strategic response and remediation to attacks can be implemented with a detailed technical classification. In the rough words of Sun Tzu, “Know your Enemy”.
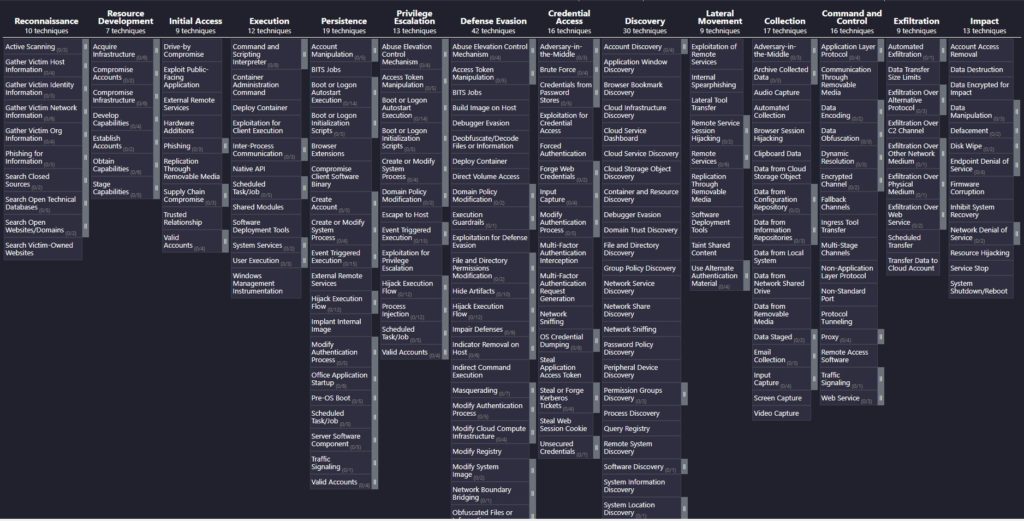
As a best practice, make sure your organization is adopting procedures and tools that leverage MITRE ATT&CK frameworks – or at least have a bridge to map to these frameworks. Some of these are specific for Mac and it requires due diligence to make sure we are using procedures and tools which specialize in the platform. Using the common library, check your software again these defined techniques by referencing your vendor’s documentation. Spot check some of these macOS defined entries: http://attack.mitre.org/matrices/enterprise/macos/. How’d we do??
Scott Morabito is a technologist and founder of TechTonic. He was trained as a computer scientist and resides in Concord MA







